Access your information system securely regardless of the time and place
Implement solutions for a secure and easy access to the information system.
Advantages of a secure remote access
In addition to a quick response, take advantage of other secure remote access benefits by using the Pulse Secure solution.
- Simple management and control
- A single access point
- Multi-factor authentication
- A detailed allocation of roles and rights
- Easy AD integration
- Activity traceability
- Client compliance checking (antivirus, security patches, etc.)
Operating systems
The secure remote access solution supports a variety of operating systems.
Podprti sistemi-Pulse Secure
Safe access for the next generation
The Pulse Secure solution provides a one-stop-shop secure mobile access, simple remote access control, and excellent user experience.
Extra knowledge can come handy
Everything you need to know about setting up a secure remote access.
Secure remote access
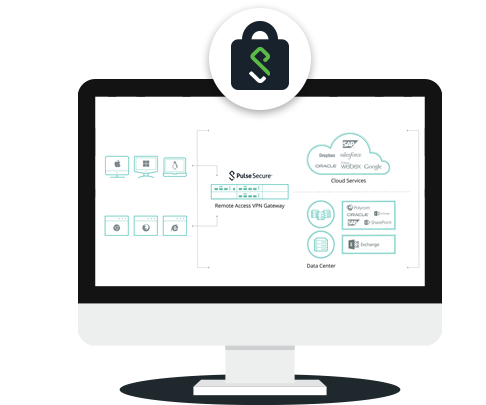
A secure remote access protects the communication path from a remote device (computer, tablet, phone) to the company’s central information system for both employees and external stakeholders. The system must allow connectivity regardless of the place and time, from any communication device.
Who are the secure remote access users and what devices can such access be used on?
The secure remote access is used by employees as well as external contractors. The device allowed to access the system must have security patches installed and meet the security requirements of the company. It is only when these conditions are met that such a device can be allowed to access important company information through a sophisticated remote access system.
Which operating systems are supported?
This type of access supports the Windows, Mac OS X, Linux, iOS, Android and Windows Phone operating systems. Virtually any device with a web browser and Internet access can connect to the system.
Where does the access end and what does the system management look like?
The central device provides a single entry point of access through which remote logins of users’ devices are completed and recorded. The system is managed through a web browser both transparently and intuitively. Granular access allocation is provided based on the person who is logging into the system and on their used device. At the same time, the system records accesses and provides a complete overview of access history and statistical views based on the time of user’s login and session.
How does the remote device/user confirm their identity?
The integration into the information system is performed in several stages.
Stage 1: During the implementation of the secure channel, the system checks for the device type (i.e. operating system) and device compliance (i.e. antivirus protection, critical patches, registry entries, etc.).
Stage 2: Once the stage 1 compliance is guaranteed, the user must enter their login attributes. We recommend the use of 2-factor authentication or certificates.
Stage 3: When all conditions from stage 1 and stage 2 have been met, the system grants access to the user based on the type of device and the user’s membership in any group included in the active directory.
Need more information?
Our cybersecurity experts will answer all of your questions related to the establishment of a secure remote access solution to your information system.
Tailor-made remote access
Create your own solution guaranteeing a secure access to the information system and include the 2FA to prevent password abuse.
PLAN - PRICE
Description
Secure remote access (PCS)
Secure remote access (PCS)
+ 2-factor SecureKey authenticator (2FA)
Secure remote access (PCS)
+ 2-factor SecureKey authenticator (2FA)
+ Pulse Workspace (BYOD)
How to guarantee safe passwords?
There are three ways to create a one-time password.
Extra knowledge can come handy
Everything you need to know about setting up a 2-factor authentication.
Which authentication method is the most adequate in view of security?
We advise against the use of local passwords or passwords from the active directory only. The high level of security is secured through the use of certificates. The next security level is ensured by the use of one-time passwords or 2-factor authentication.
What are the characteristics of 2-factor authentication?
There are three login parameters when it comes to 2-factor authentication. When logging into the system, the user enters their username (1) and personal PIN code (2). When the system verifies both parameters as correct, the user enters a unique password (3) at the last stage of the login. This unique password is a password generated by an application (mobile authenticator) or a dedicated device (password-creator); also, it can be the password the user received via a text message (SMS).
How does the remote device/user confirm their identity?
The integration into the information system is performed in several stages:
Stage 1: During the implementation of the secure channel, the system checks for the device type (i.e. operating system) and device compliance (i.e. antivirus protection, critical patches, registry entries, etc.).
Stage 2: Once the stage 1 compliance is guaranteed, the user must enter their login attributes. We recommend the use of 2-factor authentication or certificates.
Stage 3: When all conditions from stage 1 and stage 2 have been met, the system grants access to the user based on the type of device and the user’s membership in any group included in the active directory.
Reduce security risks
Security risks are brought into the organisation by users of the information system. We would be happy to review your case and advise on the choice and implementation of an optimal technological solution that is both friendly and perfected in terms of function.
Our competency advantages
Partners in the field of technology
We work with global leaders in specific technology segments.