
IoT or Internet of Things
The Internet of Things is present in a variety of segments from connected homes and cities, to connected vehicles and healthcare interfaces, to devices that track an individual’s behavior and use the data collected for future services.
It focuses on the use of sensors and communication technologies built into physical devices, enabling them to be tracked and managed over the Internet.
IoT solutions require advanced communication platforms and cloud solutions that enable full integration of devices, networks, gateways, applications, and services. This means that there is extensive exposure to potential vulnerabilities at various levels that constitute a playground for attackers.
Challenges in protecting IoT devices
The IoT faces difficult challenges, requiring comprehensive protection that extends across devices, gateways, and the cloud.
Safe IoT device life cycle
Unlike multifunction computers, IoT devices are generally more dedicated computers for a particular task. Trend Micro IoT Protection (TMIS) focuses on the state of initialization and lifecycle operation and provides two main features: threat / anomaly detection and system protection.
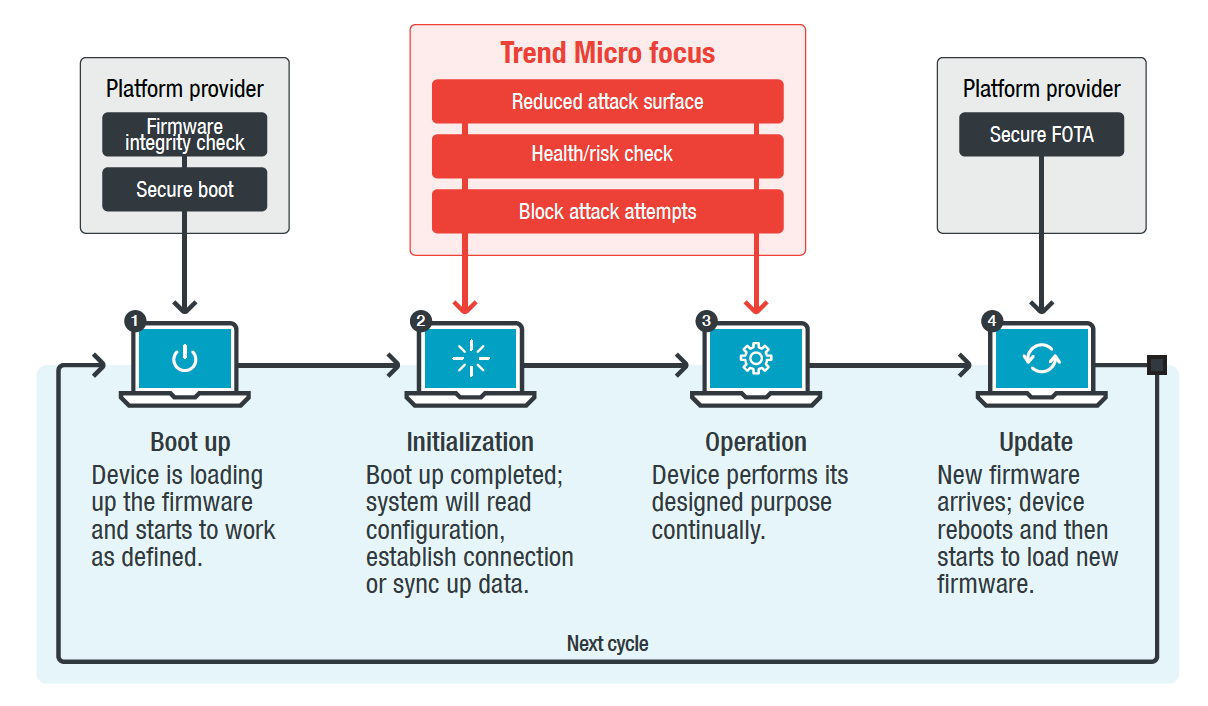
Benefits of Trend Micro IoT protection
Comprehensive protection of IoT solutions that require advanced communication platforms and cloud solutions.
Want to know more about Trend Micro IoT solutions?
Ask our security solutions expert and get advice on how to provide cybser security in both IT and OT environments.
How does Trend Micro IoT protection work?
Unlike traditional antivirus products, IoT device users are not allowed to install security solutions on devices that do not have a user interface.
TMIS can be integrated (preloaded) into the IoT of the device in the development cycle phase of the device (before shipment).
Communicates with the back-end server providing the client’s TMIS cloud services.
The security status of the device is monitored and managed via the TMIS web console.
APIs support the creation of new services and customization of the management console.
Three pillars of security
Improve protection efficiency and accuracy.
1. Discovery
The anomaly detection system collects various information to analyze large amounts of data and detect possible anomalies. The system evolves over time.
2. Security
The whitelist is created and updated automatically with TMIS in different phases. Developers of IoT devices can manage white sheets themselves manually in the development phase depending on the knowledge of their devices. The white sheets are updated to improve the efficiency and accuracy of protection even after the device is in use.
3. Management
With the help of the management console, it is possible to remotely monitor the security status of IoT devices. The threat detected by the TMIS client is displayed in the online management console along with detailed records that are useful in tracking problems.
Trend Micro comprehensive IoT protection
Six steps of IoT technology and services.
In the first step, the data is collected on sensors, followed by their processing and in the third step, it is sent to the network via a network gateway. In the fourth step, the obtained data is converted into useful information. These are used in smart applications to improve efficiency. In the last step, we come to intelligent services that exploit the output information of smart applications.
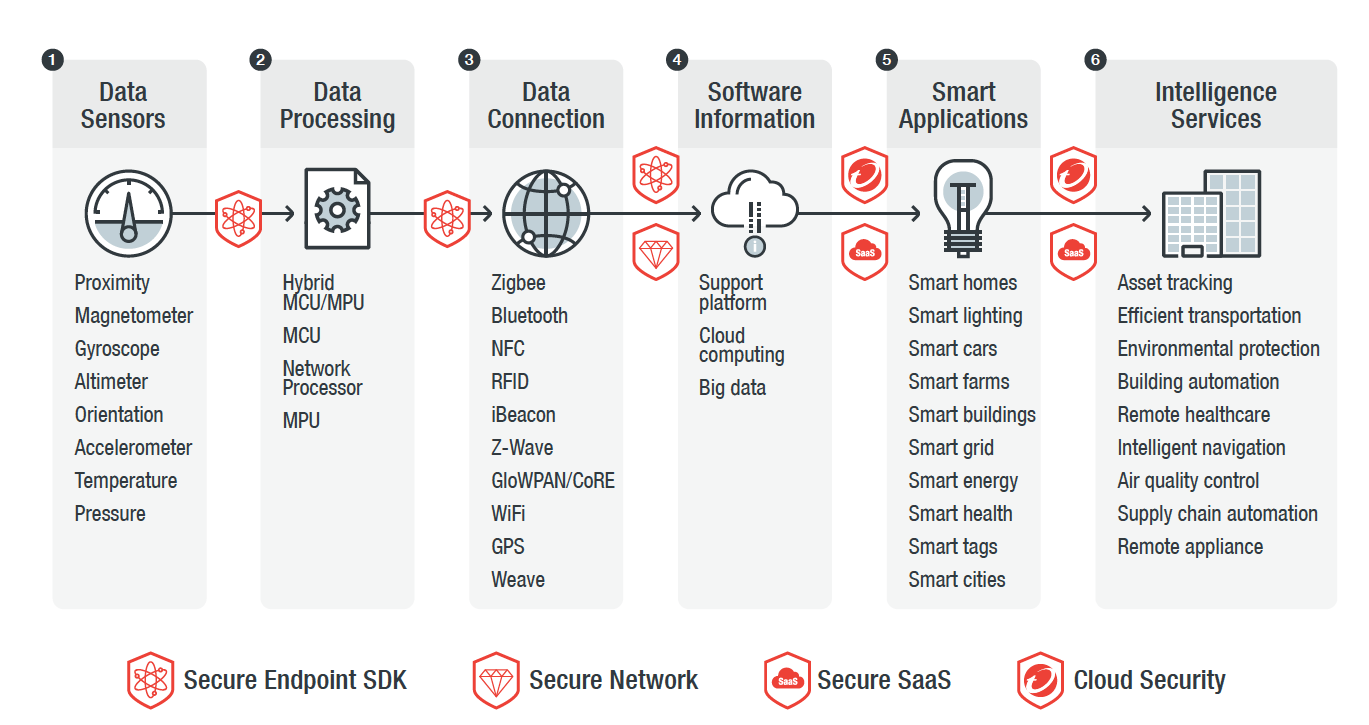
Up to and including the fourth step, it takes care of the security of TMIS with its SDK. In the data connection phase, we perform protection with the help of the Deep Discovery Inspector system, which helps visibility in the network. Server infrastructure protection is provided by the Deep Security solution, and comprehensive cloud protection is provided by the CloudONE solution.
Secure your ICS environments
Ensure network segmentation and the critical operation of critical resources with Trend Micro solutions for comprehensive protection of the OT environment, based on the most widespread industrial protocols.
Prevent intrusions and protect older, closed systems that are not connected to the Internet.
Trustworthy partner
We find solution that best fits your needs for functionality, security and maintainability.


















